**JNDI Injection — The Complete Story** ⌘ Read more
6 days ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**JNDI Injection — The Complete Story** ⌘ Read more
6 days ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Hundreds of companies’ internal data exposed — Part 2: The FreshService misconfiguration** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**HacktheBox Starting Point: Explosion Walkthrough** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**5 Ways I Can Find Your Deleted Files as An Ethical Hacker!** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**For Business Reasons | TryHackMe Write-Up** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**BSQL Injection Shenanigans** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Bypassing UAC** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**My LLM Bug Bounty Journey on Hugging Face Hub via Protect AI**
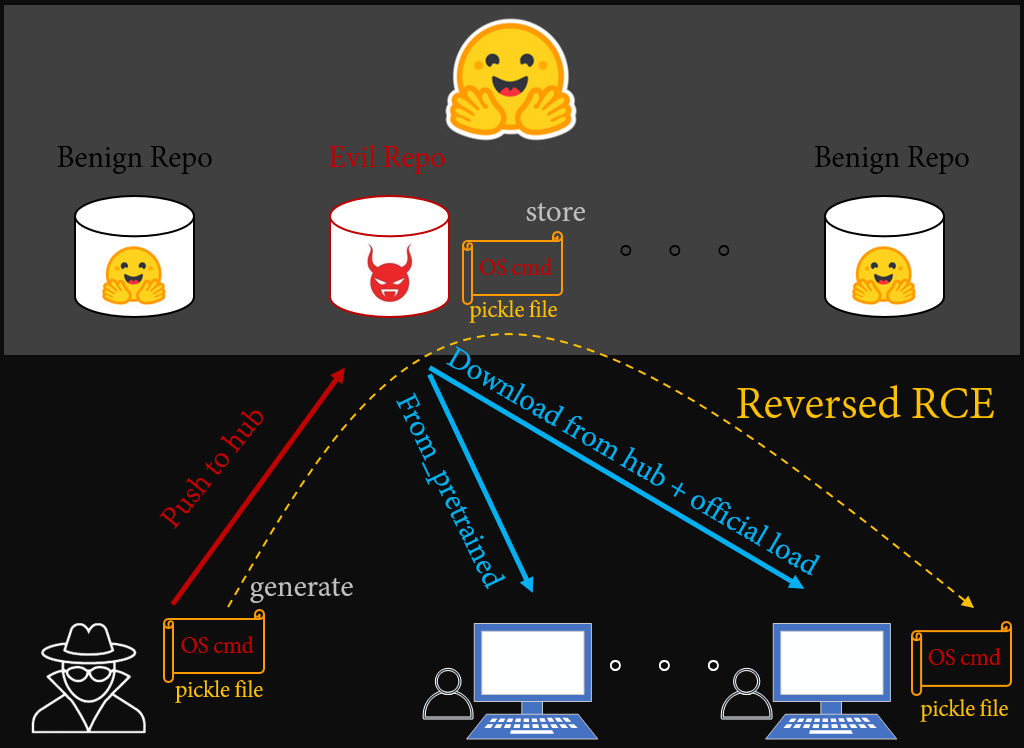
From Informative Rejection to Black Hat Briefing
Continue reading on InfoSec Write-ups »
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Hacking into 30+ tesla cars around the world using a third party software** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Creative | TryHackMe Write-Up** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Hook, Line, and Sinker: Navigating the Waters of Phishing Attacks in 2024** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**My Hunt: Discovering Microsoft Bugs**
Navigating the Terrain of Microsoft’s Software: Insights from a Bug Hunter
Continue reading on InfoSec Write-ups » ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**A Guide To Securing Your Remote Access Using SSH Keys** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**WolvCTF 2024: Forensics Challenges** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Defense against Ransomware**

Cyber-attacks, malware, and aspects of ransomware.
Continue reading on InfoSec Write-ups » ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Hacking Web Meeting/Webinar App** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Privilege Escalation Using SCIM Provisioning** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Admin Account Takeover** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Sensitive data leak using IDOR in integration service** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Understanding Zero Trust Architecture: A New Paradigm in Cybersecurity** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**HackTheBox Academy: Privilege Escalation** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Incident Response: A Comprehensive Guide for Businesses and Cybersecurity Professionals** ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Unlocking ChatGPT’s Internal Prompts: A Guide to Reverse Engineering AI Conversation Models**

Discover how to reverse engineer ChatGPT’s internal prompts, unraveling the st ... ⌘ Read more
1 week ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**AWS S3 Bucket Misconfiguration Exposes PII and Documents of Job Seekers** ⌘ Read more
2 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Honeypots 101: A Beginner’s Guide to Honeypots** ⌘ Read more
2 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**No Dev Team? No Problem: Writing Malware and Anti-Malware With GenAI** ⌘ Read more
2 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**The Diamond Model: Simple Intelligence-Driven Intrusion Analysis**
Elevate your cyber threat intelligence analysis with the Diamond Model. This full guide will teach you everything to start.
Continue reading on InfoSec Wr ... ⌘ [Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Analysis of Competing Hypotheses: How to Find Plausible Answers**
This guide will help you discover the power of the Analysis of Competing Hypotheses technique and learn how to analyze intelligence…
Continue reading on Info ... ⌘ [Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Devvortex Hackthebox Walkthrough** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Port Scanning for Bug Bounties** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**TryHackMe - Mr. Robot CTF** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Threat Modeling: A Staple of Great Cyber Threat Intelligence**

Learn what threat modeling is, why it is important, and how to perform using STRIDE, DREAD, PASTA, Attacks Trees, and VAST in this guide.
Continue reading on InfoSec ... ⌘ [Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**How to Optimize Data Sources: Collection Management Framework**

Discover the best way of collecting intelligence in this complete guide to collection management frameworks.
Continue reading on InfoSec Write-ups »
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Should You Invest In Cybersecurity Degrees or Certifications For Your Career ??**

My advice to help you in this career decision.
Continue reading on InfoSec Write-ups »
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Reading Between the Lines of Code: Ziraat_Stealer** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Securing Your Data in the Cloud** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Think You’re Talking to Real Customer Service? Think Again: Unveiling the Customer Service Scam** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Improve Your Security Skills with OWASP Juice Shop!** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Is That Really Your Bank Calling? Unraveling the Web of Vishing Scams!** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Private Interact.sh server setup with a web dashboard** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Understanding 403 Bypass: A Critical Vulnerability in Web Application Security** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Hack Stories: Hacking Hackers EP:3**

The Cybersecurity World is Not As Big As You May Think
Continue reading on InfoSec Write-ups » ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Mastering Shodan Search Engine** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Email Verification Bypass via Remember Me** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Exploiting Symlinks: A Deep Dive into CVE-2024–28185 and CVE-2024–28189 of Judge0 Sandboxes**

Explore the intricate vulnerabilities CVE-2024–28185 and CVE-2024–28189 in J ... ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Typo Trouble: Exploring the Telegram Python RCE Vulnerability** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Active DNS Recon using AXIOM** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Information Disclosure: Story of 500€ + 400$ Bounty** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Demystifying Password Cracking: Attacks and Defence Strategies** ⌘ Read more
3 weeks ago
💬 Reply
![]() infosec-write-ups-medium
infosec-write-ups-medium
**Race Condition and Broken Access Control on Developer Dashboard** ⌘ Read more
3 weeks ago
💬 Reply